Firefox Certificate Problem
If you are using Firefox 3 (and many people are now beginning to), you will notice that if FF does not like the site's certificate it will stop you dead in your tracks.
You can get past this page with about 4 steps but this would easily scare or confuse most web users.
I'm not going to go into any detail about the whys and wherefores because there are plenty of comments on the internet about it already. In fact this behaviour started with FF2 but it manifests there as a popup that allows users to easily continue should they so wish. In FF3 the solution is far more draconian. For the record I think this is a good thing but that is not what I want to discuss here.
Why does Firefox have an issue with what appears to be a perfectly good installation of SSL certificates?
The main reasons are:
- expired certificate
- self-certified certificate
- trust chain unverifiable
For the first issue the answer is easy - renew your certificate.
For the second issue there is no easy answer because as a website owner you are basically being forced to buy a certificate from someone like Verisign or Thawte as opposed to simply generating your own. The exception to this is of course if you are using the certificate in controlled environment like an Intranet. In this case you could deploy the certificate onto each of your users PCs so that they automatically get to the secured page.
Now the final issue - the one we fell foul of.
The so called trust chain required by FF is basically a 'double-hop' authentication to the root certification authority (in our case VeriSign). So effectively your browser is being told that the certificate you claim to have has in fact been issued by the issuing authority as you claim. Internet Explorer does not make a fuss about this. FF on the other hand, does. The key to this is the presense of a certificate called an Intermeidate CA certificate.
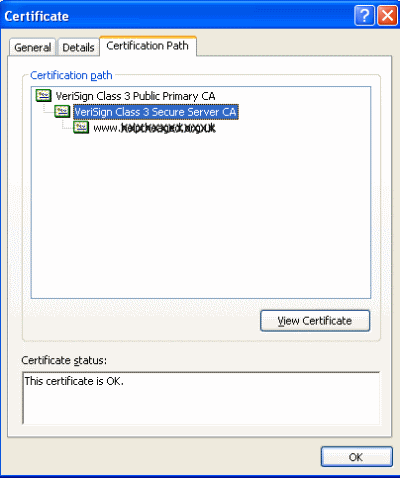
I needed to install another Intermediate CA.
I looked at the Verisign site - which is the issuing authority for our website.
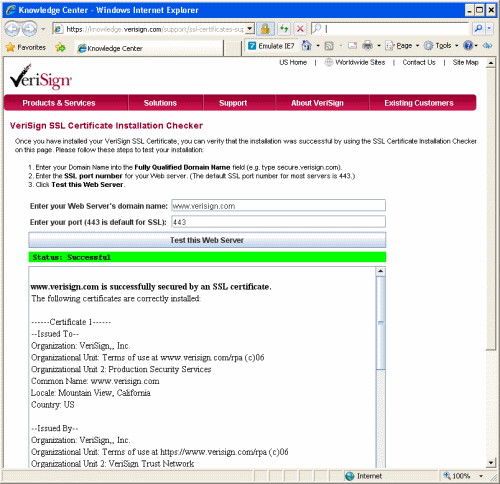
They have an interesting tool to check if your certificate is installed correctly at https://knowledge.verisign.com/support/ssl-certificates-support/index?page=certchecker.
You need to download the java plugin to get this to work.
When I first ran it, it confirmed that the intermediate CA 'could not be found'.
Luckily they provide an intermediate certificates for download.
So I downloaded that and then followed the instructions and ....uh-oh - wait a minute.
Apparently they expect you to install the certificate in IIS. But you've already got one installed for your site so the only options available are Renew, Delete, Replace. There is no 'Add'. So the instructions were hopeless.
So I tried something else.
I opened MMC.exe and added the certificates plugin for the web server.
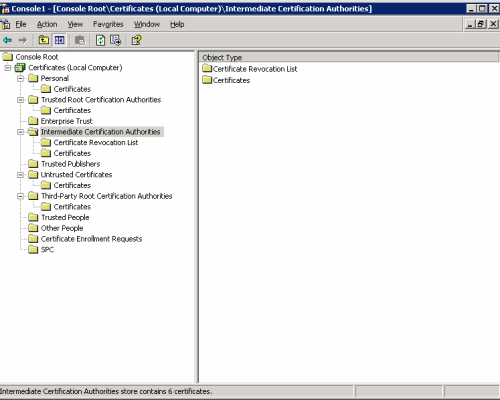
This showed me all the certificates installed on teh web server. Interestingly I could not find the Intermediate CA even in the Intermediate CA folder. Basically I suspect the IIS creates it 'by default' within the website certificate and that is whey IE (both Microsoft) 'sees' the trust chain. It just assumes it is there.
Anyway I right-clicked on teh certificates top level and chose Import.... I browsed to the text file containing the Intermeidate CA certificate and chose for the import to automatically detect where the certificate should go.
It didn't work. FF didn't like it, and when I ran Verisign's tool it wasn't too impressed either. It still could not find the certificate.
So I tried the import again. This time I ensured that the certificate was imported into the Intermediate certificates folder. When the import finished there it was.
The instructions from Verisign say that an IIS restart is required for the new certificate to take effect.
I agonised over this for a few minutes because I was afterall working on a production server and a reset would take a number of websties offline if only for a minute.
But a few minutes later I thought I'd try FF again and surprise surprise, the page loaded! No IIS reset required.
To make double sure I ran the Verisign tool. It too indicated the installation was fine.